Back in 1979, just out of grad school, I got my first real job working as a software developer (we used to be called “programmers” in the olden days). I learned the C programming language then and did my software development on a Digital Equipment Corporation PDP-11/70 minicomputer running 6th edition UNIX. And for the first time, I was using a multiuser computer which could be crashed by a non-privileged user doing non-privileged things. I mean, an error in Charlie’s or Mike’s (never mine!) code could crash the whole machine. “Why doesn’t the operating system protect against such things?”
As I said, that was 1979. 30 years later, in September 2009, my friend David Strom, citing a report from the SANS Institute on top cyber security risks, wrote “Unpatched applications are the real threat.” Are they? I reiterated what I asked 30 years ago: “Why doesn’t the operating system protect against such things?”
Quoting the SANS report, he writes, “Most web site owners fail to scan effectively for the common flaws,” and “TippingPoint reported that vulnerabilities that were more than two years old were still waiting for patches.”
Patching? The SANS report is a good reminder of what can and should be done in the short term. But, it is clear that, while patching is useful (I won’t even write “important”), it should only be important for data integrity or program availability, not for security of the data or of the system. The hardware and software system should protect against such things. The computer science world has been flirting with “trusted computing” and trusted operating systems for years. The “real threat?” Operating systems we still cannot trust to effectively control and contain user-level applications.
12/23/09
“Senate Panel Agrees with Avolio”
Okay, the headline actually says, Senate Panel: 80 Percent of Cyber Attacks Preventable, but basically the panel said what I have said in over 60 different blog entries (according to this search on “same old”). The article by Kim Zetter opens with this statement:
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
If network administrators simply instituted proper configuration policies and conducted good network monitoring, about 80 percent of commonly known cyber attacks could be prevented.This October 2009 Wired article is an example of what I’m (and they are) talking about. The headline states “Time Warner Cable Exposes 65,000 Customer Routers to Remote Hacks.” It goes on to mention “The device is installed with default configurations.” (See what I wrote about default configurations and what to do about them at Top Ten Security Threats, but in this case it would not have helped as Time-Warner did not permit changing the router in question.)
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
Evernote
Many have reviewed Evernote, and months have gone by since I first mentioned it in my blog. I will briefly discuss how and why I use Evernote and point to some other helpful blog posts.
In my quest to get things done, I used to make use of email and of my PDA to keep task lists and to remind me of things I did not want to forget. (As the senior Dr. Henry Jones says, in Indiana Jones and the Last Crusade says, “I wrote them down in my Diary so that I wouldn’t have to remember.”) If I found something on the web that I wanted to download or read, but didn’t have the time to deal with at the moment, I would send myself emails with the subject “tryme” or “readme.” When I got home in the evening, I would take care of them by actually downloading something I wanted to try or reading something I wanted to read (on my iPod touch screen, or by printing).
Also, as I have mentioned, I make extensive use of Notes in my PDAs; I used to use Memos on Palm, and now Notes on my iPod touch. Then I started reading about Evernote. I read 7 Ways to Use Evernote. I also read 9 Ways I use Evernote, and How To Use Evernote to Remember Everything, Part 1 and Part2.
I started using Evernote to capture the things I previously emailed. I did this on my home PowerBook Pro of on mywork MacBook Pro. The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch.
The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch. 
The more I use Evernote, the more I like it, and the more ways I find to use it.
In my quest to get things done, I used to make use of email and of my PDA to keep task lists and to remind me of things I did not want to forget. (As the senior Dr. Henry Jones says, in Indiana Jones and the Last Crusade says, “I wrote them down in my Diary so that I wouldn’t have to remember.”) If I found something on the web that I wanted to download or read, but didn’t have the time to deal with at the moment, I would send myself emails with the subject “tryme” or “readme.” When I got home in the evening, I would take care of them by actually downloading something I wanted to try or reading something I wanted to read (on my iPod touch screen, or by printing).
Also, as I have mentioned, I make extensive use of Notes in my PDAs; I used to use Memos on Palm, and now Notes on my iPod touch. Then I started reading about Evernote. I read 7 Ways to Use Evernote. I also read 9 Ways I use Evernote, and How To Use Evernote to Remember Everything, Part 1 and Part2.
I started using Evernote to capture the things I previously emailed. I did this on my home PowerBook Pro of on mywork MacBook Pro.
 The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch.
The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch. 
The more I use Evernote, the more I like it, and the more ways I find to use it.
9/21/09
Be Careful With Those Firefox Extensions
People who know me from my consulting and teaching days, or who have read my web site from my consulting days, have read my blog. or have been in a class I taught, know that I am a pretty cautious guy when it comes to the Internet.
Today, via web mail, I was checking my personal (non-APL) email. I saw one of the messages was from Hallmark Postcards, saying I had a postcard from someone. Now, I already knew that it was spam, just from that information. What I should have done was just check the box next to it and click on “Report Spam.” Instead I opened the message. No problem. I saw the URL for the card, so I “hovered” my mouse over it. It was “postcard.exe.” Into the spam folder with you, sucker!
A few minutes later I got a call from someone in the IT department here at APL. One of our security devices indicated I tried to download that file. It blocked the download and reported it. Now, the Windows executable would have done nothing on my Mac, and recall I did not click on it to download it. What had happened?
I looked through the add-ons and extensions I had in Firefox. Sure enough, amidst the security-related add-ons, I also had added Interclue, “Your Personal Link Preview Multitool.” It promises, “Before you click the link: Hover your mouse pointer over the link, and a Linkclue icon will appear. Rest your mouse on the icon, and up pops an enhanced summary of the linked page.”
Hmmm. I don’t think it actually tried (or tries) to download anything. I think that our security software saw this in the stream and triggered an alarm. (On the other hand, what does it mean to “preview” an executable? I’m not sure, and I didn’t need Interclue enough to want to keep it. I uninstalled it and restarted Firefox.
Update
I heard from my co-worker in the IT department. He writes:
Today, via web mail, I was checking my personal (non-APL) email. I saw one of the messages was from Hallmark Postcards, saying I had a postcard from someone. Now, I already knew that it was spam, just from that information. What I should have done was just check the box next to it and click on “Report Spam.” Instead I opened the message. No problem. I saw the URL for the card, so I “hovered” my mouse over it. It was “postcard.exe.” Into the spam folder with you, sucker!
A few minutes later I got a call from someone in the IT department here at APL. One of our security devices indicated I tried to download that file. It blocked the download and reported it. Now, the Windows executable would have done nothing on my Mac, and recall I did not click on it to download it. What had happened?
I looked through the add-ons and extensions I had in Firefox. Sure enough, amidst the security-related add-ons, I also had added Interclue, “Your Personal Link Preview Multitool.” It promises, “Before you click the link: Hover your mouse pointer over the link, and a Linkclue icon will appear. Rest your mouse on the icon, and up pops an enhanced summary of the linked page.”
Hmmm. I don’t think it actually tried (or tries) to download anything. I think that our security software saw this in the stream and triggered an alarm. (On the other hand, what does it mean to “preview” an executable? I’m not sure, and I didn’t need Interclue enough to want to keep it. I uninstalled it and restarted Firefox.
Update
I heard from my co-worker in the IT department. He writes:
What our network systems saw is the following exchange between your host and the remote serverI agree. Avoid this Firefox extension.Request from your host:This, of course, shows your host asking for postcard.exe and our Websense device referring your host to a block page thereby preventing the download. Your Firefox plug-in wants to provide a preview of the web page. To provide a preview, it apparently downloads the web page (or at least part of it). Otherwise, how would it know what the page looks like so it could provide a preview? It looks like a rather dangerous plug-in, one designed for a more friendly Internet.
GET /postcard.exe HTTP/1.1
Host: nn.nn.nn.nn
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US;
rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Cache-Control: no-cache
Pragma: no-cache
Reply to the request:
HTTP/1.1 302 Moved Temporarily
Date: Mon, 21 Sep 2009 14:05:36 GMT
Connection: close
Via: HTTP/1.1 localhost.localdomain (Websense-Content_Gateway/7.1.2 [c s f
])
Location:
http://nn.nn.nn.nn/cgi-bin/blockpage.cgi?ws-session=3741857785
Content-Length: 0
9/12/09
Safeguard your Notebook Computer
No matter how careful you are about physically protecting your small notebook computer, you need to plan for the worse. A few months ago, The Unofficial Apple Weblog (TUAW) had an article 9 things I learned from almost losing my MacBook Air. It is Mac-specific in the details, but no matter whether you have a MacBook, a Windows notebook, or something else, computers are getting smaller, disks are getting larger, and that raises the vulnerability to information loss. And no matter what you think, you have data on your computer that, in the wrong hands, could cost you money.
It reminded me of a few columns, not Mac-specific, I wrote years a few years back:
It reminded me of a few columns, not Mac-specific, I wrote years a few years back:
9/11/09
9/9/09
New Software: iTunes 9.0 and iPod touch 3.1 update
I’ll make this short and sweet. I updated my iPod touch software to 3.1 and my iTunes to 9.0, both announced today (among other things you can find on the Apple Website. I installed iTunes thorough the iTunes program, checking for software update. It downloaded iTunes 9.0, Quicktime Player 7.6.4, and restarted my PowerBook.
I started iTunes. Anytime I accessed the iTunes store it crashed. So, I manually downloaded iTunes 9.0. It works fine now.
See 3.1 features and iTunes 9.0 features for more information.
I started iTunes. Anytime I accessed the iTunes store it crashed. So, I manually downloaded iTunes 9.0. It works fine now.
See 3.1 features and iTunes 9.0 features for more information.
8/26/09
Apps on my iPod touch
This may be of no interest to anyone, or maybe only to one friend who just purchased his first Mac and his first iPod touch, but I figure if I write it for one, I might as well get mileage out of it.
Unless otherwise stated, all apps were free of charge from the App Store (iTunes Store). Some I bought via iTunes on my Mac, and some I bought from my iPod and the App Store app.
On the bottom of each screen are the things I use most often, Mail, Calendar, Contacts, and Music.
Screen 1


Unless otherwise stated, all apps were free of charge from the App Store (iTunes Store). Some I bought via iTunes on my Mac, and some I bought from my iPod and the App Store app.
On the bottom of each screen are the things I use most often, Mail, Calendar, Contacts, and Music.
Screen 1

- Safari, Facebook, Google, Twitter, Calculator, Settings all obvious. I do often check FB and Twitter in the morning and evening.
- Weather. The Weather Channel powered by Yahoo! I check the weather every morning. I also have the weather for places friends and family are.
- Notes. I use a lot! References, etc. I copied Memos in text form from Palm Desktop and put them into the Notes in Mail.app on my Mac. Need 3.0 update of iPod software for this. Worth the $9.99.
- Google Maps. I entered my home access points MAC addresses into Skyhook, so it knows my location at home. Most outside networks show up (APL, coffee shops, etc.)
- BibleReader, and eReader—I use daily.
- mSecure. I bought this. It is an encrypted lockbox for passwords, and other info I want to keep safe but cannot just remember. There is a free desk application so that I can create in either place, and I can backup.
- FighterVerses. Google “fighter verses john piper”. I got this from a tweat of his.
- Skype and LinkedIn. I can text chat or audio chat via Skype and a microphone (which I bought). I never had (have on my Mac though). But I have the mic with me if I want/need to! 🙂 I check LinkedIn but rarely use it. (I am moving both off of my first page.)
- Evernote. I need to blog on this but Google search it. I am now using it on my iPod, home Mac, and work Mac, and syncing them via the Internet.

- Clock. I rarely use the alarm and timer, though I have used both. I use it to keep time zone info for cities with friends in (Odessa, Bangalore, Vienna, Chiba, etc.)
- iTunes, App Store, obviously for purchases when not at my home Mac.
- Photos. Rarely use. Sometimes for capturing screen-shots (like these) and them emailing to myself to incorporate into something else (like this).
- IM+ Lite. IM client for AIM, etc. Rarely use.
- TouchTerm and VNC for remotely connecting to other machines, Rarely use.
- TWC and Weatherbug. When I want to see a weather map, hourly and 1- day forecast, and weather cameras I use these.
- ShareContact. Rare. But, in Contacts, if you want to share someone’s contact info with someone else it will send it via email as a vcf attachment. I know a bunch of folks who would not know what to do with it. This sends text in the message body.
- Stanza is like eReader. I think I was testing it. Don’t need it.
- iTalk is a voice recorder. You need a mic.
- Mars Hill. I wanted to see what their app did. I don’t use it.
- PNC is an app to get to my back account, etc.
- FedEx is obvious. I don’t use it.
- Voice Memos, obvious. Came with the mic..
- SkyVoyager, etc., were free on July 20 to celebrate the anniversary of the first moon landing.
- AllRecipes. Cute, interesting, maybe useful.
- B&N; is a B&N-branded; eReader. I don’t mean it is an eBook reader; I mean it is eReader with a B&N; wrapper. I’ve deleted it, but one might want it for the free dictionary and books.
- This is True. A daily dose of www.thisistrue.com. See
- Ambiance Lite. Cute. Different cover-noises. Rain on rood, rain on car roof, highway, train, etc.
- Amazon.com, NY Times, USA Today, Stocks (which I don’t use, but is not removeable), all obvious.
- TV.com, YouTube, linked to those video sites.
- Videos are videos that I downloaded via iTunes on my Mac which converts to size for iPod touch. I’ve got videos saved from YouTube, movies I bought and illegally converted, etc.
- Drinks Free. All sorts of drink recipes.
- DocsToGo. Paid for it for Palm and I may have had to pay something for the version for the iPod/iPhone. Word, Excel, PowerPoint. There is a Mac-side application and this syncs with that.
- Pingle is a central app for updating status or making microblogs on LinkedIn, Twitter, FaceBook, etc.
- Games. Free ones. Mostly got for kids. I have to be incredibly bored to play any of them
8/24/09
Pointer to “10 free tools for getting work done on your Mac”
This is an excellent article, especially for those who are new to Mac.
10 free tools for getting work done on your Mac.
The last thing he mentions is ClamXav free antivirus for Mac. And I still say—sanity-checked by my Mac Genius, Kevin—you don’t need AV on your Mac unless you are compelled to by your management.
10 free tools for getting work done on your Mac.
The last thing he mentions is ClamXav free antivirus for Mac. And I still say—sanity-checked by my Mac Genius, Kevin—you don’t need AV on your Mac unless you are compelled to by your management.
8/20/09
My Move to Mac, 4 Years Ago
I’ve talked to two people in the past week about switching from PC to Mac. I am not a Mac zealot. I just made the move from using Microsoft PCs to using Apple Macs in August 2005, when my PC turned on me, and I’ve never looked back.
I started my pc2mac label in this blog way back then, Since I talk about a lot of other Mac-related things now, I decided to list pointers to initial blog entries from when I made the move.
I started my pc2mac label in this blog way back then, Since I talk about a lot of other Mac-related things now, I decided to list pointers to initial blog entries from when I made the move.
- Dude, your getting a Mac
This describes “the straw that broke the camel’s back.” - After Windows, What?
These are the deliberations I went through when I decided to dump Windows. - PowerBook Day 1 and Following
These were my initial reactions after getting my first Mac. - Mac Browsers and Instant Messengering.
I explore these aspects of my new system. - Moving to Mac Email.
- Mac Calendaring and Address Book
8/13/09
Strom Reviews Sendmail’s Senturion
My friend David Strom recently posted a video review of this enterprise e-mail management product from Sendmail, Inc. His review is at Webinformant.tv.
Sendmail has come a long way since I wrote this review of Sendmail Pro, over 9 years ago!
Sendmail has come a long way since I wrote this review of Sendmail Pro, over 9 years ago!
8/1/09
Time Machine System Restore
I have an 80GB disk waiting to be installed to upgrade my aging, bit still small, light, and useful PowerBook G4. Last week, I wrote to a friend, “Would have been a good day to swap disks out. :-)”
The PB was working fine. As I mentioned in System Back-ups, I have an external FireWire drive onto which TimeMachine backs up. Last
backup 10:30 that “fateful” morning. At 11 or so I decided I should run SuperDuper!, which I use to have a bootable copy of my PB. (I don’t do that automatically; the last time I did that was 2 weeks earlier, but Time Machine does the day-to-day—really hour-to-hour—file copy stuff.) Before I did that, I decided to check it out with Disk Utility.
I ran DU and got the error “Keys out of order… The Volume Macintosh HD could not be repaired. Error: File verify or repair failed. You are so hosed.” (I made up that last bit.)
I booted off of the FireWire Leopard partition, used Disk Utility on it and it still could not fix it. Now, I was a bit annoyed. There should be nothing in software that should hurt the disk structure so much that software cannot fix it. And I mean software from the vendor.
I was told that Disk Warrior would fix errors on the disk including this “Keys out of order.” A friend, who seems to have everything, had an unopened copy of Disk Warrior, which I tried. No joy. It could not fix it.
Hmmm. I was starting to think of that 80 GB disk sitting in its wrapper. But, that would entail spending time and tools to open my PowerBook. No, that would wait for another day.
I tried to Restore (in Disk Utility) from my Leopard partition I was running off of (FireWire drive, remember), to my Mac HD. It said their wasn’t enough space! Okay, I erased my Mac HD! There! Said the same thing.
Plan C, now. Restore from Time Machine. Following Apple’s Instructions, I booted from the install DVD, picked Restore from Time Machine, and… it worked. It worked beautifully.
Whew.
The PB was working fine. As I mentioned in System Back-ups, I have an external FireWire drive onto which TimeMachine backs up. Last
backup 10:30 that “fateful” morning. At 11 or so I decided I should run SuperDuper!, which I use to have a bootable copy of my PB. (I don’t do that automatically; the last time I did that was 2 weeks earlier, but Time Machine does the day-to-day—really hour-to-hour—file copy stuff.) Before I did that, I decided to check it out with Disk Utility.
I ran DU and got the error “Keys out of order… The Volume Macintosh HD could not be repaired. Error: File verify or repair failed. You are so hosed.” (I made up that last bit.)
I booted off of the FireWire Leopard partition, used Disk Utility on it and it still could not fix it. Now, I was a bit annoyed. There should be nothing in software that should hurt the disk structure so much that software cannot fix it. And I mean software from the vendor.
I was told that Disk Warrior would fix errors on the disk including this “Keys out of order.” A friend, who seems to have everything, had an unopened copy of Disk Warrior, which I tried. No joy. It could not fix it.
Hmmm. I was starting to think of that 80 GB disk sitting in its wrapper. But, that would entail spending time and tools to open my PowerBook. No, that would wait for another day.
I tried to Restore (in Disk Utility) from my Leopard partition I was running off of (FireWire drive, remember), to my Mac HD. It said their wasn’t enough space! Okay, I erased my Mac HD! There! Said the same thing.
Plan C, now. Restore from Time Machine. Following Apple’s Instructions, I booted from the install DVD, picked Restore from Time Machine, and… it worked. It worked beautifully.
Whew.
7/15/09
Schneier on North Korean Cyberattacks
The complete text is at http://www.schneier.com/blog/archives/2009/07/north_korean_cy.html.
Some great quotes:
Some great quotes:
- "What [the President] didn’t add was that those infections occurred because the Air Force couldn’t be bothered to keep its patches up to date. … Even this current incident is turning out to be a sloppily modified five-year-old worm that no modern network should still be vulnerable to."
- "Securing our networks doesn’t require some secret advanced NSA technology. It’s the boring network security administration stuff we already know how to do: keep your patches up to date, install good anti-malware software, correctly configure your firewalls and intrusion-detection systems, monitor your networks. And while some government and corporate networks do a pretty good job at this, others fail again and again."
- "The news isn’t the attacks, but that some networks had security lousy enough to be vulnerable to them."
7/10/09
Spammers need grammar lessons
“Hello from Ms vivian shaka, I am writing with the earnest prayer that my attention will meet favorably with you.”
I really want to reply and say, “Hey, Viv! What the heck does that even mean?! ‘My attenion will meet favorably with you,’ indeed!”
I really want to reply and say, “Hey, Viv! What the heck does that even mean?! ‘My attenion will meet favorably with you,’ indeed!”
7/6/09
Masked passwords must go
This article in The Register, Masked passwords must go, reports recommendations from "Usability expert Jakob Nielsen and security expert Bruce Schneier" saying that "both think websites should stop blanking out passwords as users type them in. They say the practice inconveniences users and delivers no security benefits."
I certainly find this to be true, and not just because I am getting older. I suspect I am not different than many of us here. I have to remember (or security hide) 6 passwords including 2 on a sponsor network. I have to change them all regularly, though not, of course, on the same schedule. And the password rules for our more secure systems and uses means I’ve had to be creative.
The idea is creativity = security. Yes, but not when it also needs to include "usability." That is always the tug-of-war, and equilibrium between the two is a good thing.
Anyway, back to the article. 1) It would be great if I could see what I type into systems and web pages here. 2) No matter what experts say that it is both secure and usable, I don’t believe that we will ever get changes as suggested in the article.
Schneier has clarified his position on this in The Pros and Cons of Password Masking.
I certainly find this to be true, and not just because I am getting older. I suspect I am not different than many of us here. I have to remember (or security hide) 6 passwords including 2 on a sponsor network. I have to change them all regularly, though not, of course, on the same schedule. And the password rules for our more secure systems and uses means I’ve had to be creative.
The idea is creativity = security. Yes, but not when it also needs to include "usability." That is always the tug-of-war, and equilibrium between the two is a good thing.
Anyway, back to the article. 1) It would be great if I could see what I type into systems and web pages here. 2) No matter what experts say that it is both secure and usable, I don’t believe that we will ever get changes as suggested in the article.
Schneier has clarified his position on this in The Pros and Cons of Password Masking.
6/19/09
iPod touch 3.0 Review
I was very glad for the 3.0 software update. I’ve wanted some of these new features since I moved from using a Palm handheld as my PDA to using an iPod touch. (See iPod touch Wishlist, and My New PDA: iPod touch. All of my “wishes” were granted except for the Task Manager.) The $9.95 (USD) was well worth it.
It is hard to decide which new feature is my #1. I don’t care, for example, about the enhancements to the Stocks app or the addition of the Voice Memos app. (I have the iTalk app, which I got when I bought a microphone from Griffin.
Here, in no special order, are my top new features, and why.
As you can tell, I am pleased with the 3.0 upgrade and was happy to spend the money.
It is hard to decide which new feature is my #1. I don’t care, for example, about the enhancements to the Stocks app or the addition of the Voice Memos app. (I have the iTalk app, which I got when I bought a microphone from Griffin.
Here, in no special order, are my top new features, and why.
- Copy and Paste. This is probably my #1 and it works with all of the Apple-supplied applications. It is intuitive, too, apparently. I did not look at the manual, first (of course). I just experimented. In a nutshell, it rocks!
I needed to copy something from a Google Calendar entry to take with me to a place with no WiFi. Standing about to walk out of the house, I clicked on Google, selected apps, then my Calendar. (I needed an entry from a shared calendar I do not sync with iCal.) I held my finger on the entry. The software wisely selected the entire text of the calendar entry. I selected Copy, hit the Home button, selected Notes, hit the plus (add) button, pasted into a new note, and I was done and on my way. I have and will use this for copying and pasting URLs from mail messages, etc. Great stuff. - Search. Wow. There is a global search of the whole iPod. (Which application data are searched is settable in Settings,General, Home, Search Results.) Globally, it shows you by application where the searched for string is. Also, individual apps have a search function built in (for example, to just search Notes.) In the Mail app, each folder allows me to search that folder, both the data on the iPod as well as the data not yet downloaded. (Pull down on the window showing the messages in a folder, to expose the search window.) In Calendar, this is in the List view.
- Notes. Some people never use Notes. As I said in and After Windows, What?, I used Memos (Notes equivalent) a lot on my Palm. I have notes with notes from meetings I want to remember, quotes I want to keep, a list of my prescriptions, the cost of the DC Metro from Greenbelt Station to L’Enfant Plaza—currently 33 Notes in all. I had some of these on my Mac, copied from my Palm. I used a trial version of some app to get them into my Notes, but had no way of adding more on my iPod without typing on my iPod. So, I was happy that this was a feature in 3.0.
Notes now syncs with Notes in the Mail app (or with Notes in Outlook). I did not use Notes in Mail, but for creation and modification for syncing to my iPod, it is great. I recently wanted to add instructions for accessing free wireless at Starbuck’s using my Starbucks card. I had 2 ways to save the information onto my iPod in a note (before going to Starbucks). 1) I could access their web page on my iPod from home and copy the information and then paste it into a new Note. 2) I could access it from my Mac and create a create a new Note in Mail that will be synced. - eMailed Calendar Events now get added to Calendsr when you click on the .ics attachment.
- iPod changes. There may be more, but one thing I noticed this morning on the way to work: there is an adjustable speed control on podcasts (1x, 2x, and 1/2x speed). This is similar to the speed control settable in iTunes before on audio books, only. This is nice. I find that many podcasts, lectures, etc., are easily understandable at 2x the speed.
As you can tell, I am pleased with the 3.0 upgrade and was happy to spend the money.
4/30/09
Gmail: Can it be trusted?
In Mail and Gmail and More on Mail and Gmail, I discuss my move to Gmail as my main avolio.com mail server.
Gmail Glitch Shows Pitfalls starts off with “When Google Inc.’s online-email service shut off for over two hours earlier this week, it brought to light concerns about whether businesses can safely rely on software that their employees access over the Internet.” The Wall Street Journal On-line article goes on to say, “… companies are finding that going online to do business-computing tasks via services like Google’s … comes with a risk: When something goes wrong, customers must sit idly while waiting for someone else to fix the problem.”
I say this is FUD. Who doesn’t have to suffer occasional outages? Servers go down, ISPs disconnect occasionally, cables get cut. Owning the servers and employing those who run them may feel safer, but I suspect does little to mitigate the risk of an outage.
Is it worth the risk? I think so.
Gmail Glitch Shows Pitfalls starts off with “When Google Inc.’s online-email service shut off for over two hours earlier this week, it brought to light concerns about whether businesses can safely rely on software that their employees access over the Internet.” The Wall Street Journal On-line article goes on to say, “… companies are finding that going online to do business-computing tasks via services like Google’s … comes with a risk: When something goes wrong, customers must sit idly while waiting for someone else to fix the problem.”
I say this is FUD. Who doesn’t have to suffer occasional outages? Servers go down, ISPs disconnect occasionally, cables get cut. Owning the servers and employing those who run them may feel safer, but I suspect does little to mitigate the risk of an outage.
Is it worth the risk? I think so.
Intolerance
I am embarrassed to say I am strangely intolerant about two things (but only two :-)), both in the PDA realm. The first, is people referring to any and every Palm Computer as a PalmPilot. As Wikipedia says,“The first two generations of PDAs from Palm were referred to as “PalmPilots”. Due to a trademark infringement lawsuit brought by the Pilot Pen Corporation, since 1998…” Back then, US Robotics manufactured the PalmPilot, and I had one. Probably, no one has a PalmPilot today, yet people still call it that.
And on the Apple discussion groups and elsewhere, people will talk about there iTouch when they mean iPod touch. Yes, even spelled with a lower-case “t.” You have an iTouch if you have an this iPod touch knock-off.
And on the Apple discussion groups and elsewhere, people will talk about there iTouch when they mean iPod touch. Yes, even spelled with a lower-case “t.” You have an iTouch if you have an this iPod touch knock-off.
iPod touch and “Shuffle Albums”
Older iPods had a feature that would allow you to shuffle songs or albums. It would play a random album in its entirety, then another, etc. This is not available on a touch (an unjailbroken touch).
What I mean by Shuffle Albums,” is really randomly find and play an entire album. I started to want this recently when “shuffle songs” would turn up a song I haven’t listened to in years. I would have a “Wow,I remember this album,” moment. This is a simple, obvious way to get this functionality.
1. I select songs to list all the songs on my iPod touch.
2. I push the “Shuffle” command.
3. I push the Next Song” command until a song comes up from an album I’m interested in.
4. I select the list of songs on the album (top righthand side)
5. I select the first song in the album
It seems like a lot to go through, but really step 3 doesn’t usually take that long before I stumble upon .. shuffle upon … an interesting album.
What I mean by Shuffle Albums,” is really randomly find and play an entire album. I started to want this recently when “shuffle songs” would turn up a song I haven’t listened to in years. I would have a “Wow,I remember this album,” moment. This is a simple, obvious way to get this functionality.
1. I select songs to list all the songs on my iPod touch.
2. I push the “Shuffle” command.
3. I push the Next Song” command until a song comes up from an album I’m interested in.
4. I select the list of songs on the album (top righthand side)
5. I select the first song in the album
It seems like a lot to go through, but really step 3 doesn’t usually take that long before I stumble upon .. shuffle upon … an interesting album.
4/22/09
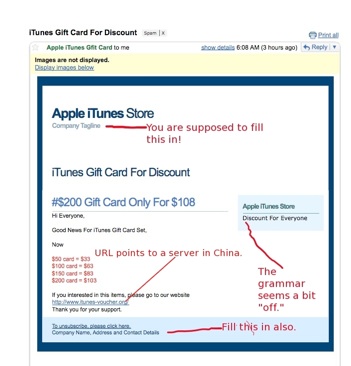
Note to a Chinese Phisher
4/14/09
On-line Backups
I have written about the importance of system back-ups many times before. I talk about it specifically in System Back-ups.
Today, in my news aggregater, Macworld reported on BackBlaze. BackBlaze is a $5/month online backup server and service for Macs and PCs, and has no limit to how much you can back up.
Also, The Unofficial Apple Weblog has a review with shiny pictures.
I’ve not tried it yet, but I intend to. The questions that have come to my mind are all the obvious ones. They answer some on their web page. For many of you, the important answer is “It is better than the backup scheme you currently have,” knowing that many of you (twice I wanted to write “most”) don’t backup at all.
If you try it, let me know what you think. I will do the same.
Today, in my news aggregater, Macworld reported on BackBlaze. BackBlaze is a $5/month online backup server and service for Macs and PCs, and has no limit to how much you can back up.
Also, The Unofficial Apple Weblog has a review with shiny pictures.
I’ve not tried it yet, but I intend to. The questions that have come to my mind are all the obvious ones. They answer some on their web page. For many of you, the important answer is “It is better than the backup scheme you currently have,” knowing that many of you (twice I wanted to write “most”) don’t backup at all.
If you try it, let me know what you think. I will do the same.
4/6/09
3/31/09
New Old Macs
Recently we purchased a few computers and I thought I would blog about that purchase. You might be thinking, “Not very interesting or exciting.” Hang in there. The recent resurgence of “PCs are less expensive than Macs” pulled this into the forefront.
I’ll not really talk about “which is cheaper.” I’ll just point you to the original article I read in this WSJ Blog entry. (Fortune Magazine via CNN also reported on it.)
Now, it has been parodied in The Joy of Tech and it has been rebuffed. I just read about one company that is doing what I am doing: buying new used, old Macs. (See Macs in the Enterprise: the Cost Factor.)
Living in our house are 3 adults and—counting my son away at school—6 children. Before this week we had 1 Mac (mine) and 5 PCs (my wife’s, my two college kids have 1 each, 1 for my son in high school, and 1 shared by the others, as well as a Linux system for storage.
First, the mother board on the Linux box when bad. After struggling with it, I decided to replace it. To replace it, I bought a Apple Power Mac G4 (my notebook is a PowerBook G4). I bought it for $99 plus shipping from Mac of All Trades. $99! A friend gave us a second Power Mac G4. The friend called me up a few days later and said Mac of All Trades had $79 Power Macs, just like the one I bought. Did I want to buy another? I did! $79 for a computer! $79 for a very usable computer. For what? For web surfing. For music downloads. For Facebooking. For You Tubing. For writing documents and otherwise doing homework.
For heavy-duty music or photo editing? No. Software development? Probably not. More than adequate? A lot more than adequate.
And I forgot this about a new Mac, old, used, or otherwise. You plug it in, turn it on, confirm security settings (they are, after all, on my home network), and it is up and on the network, working. I mean in less than 5 minutes.
So, when the other new, old Mac shows up, it will be: 5 PCs and 4 Macs. So far. 🙂
I’ll not really talk about “which is cheaper.” I’ll just point you to the original article I read in this WSJ Blog entry. (Fortune Magazine via CNN also reported on it.)
Now, it has been parodied in The Joy of Tech and it has been rebuffed. I just read about one company that is doing what I am doing: buying new used, old Macs. (See Macs in the Enterprise: the Cost Factor.)
Living in our house are 3 adults and—counting my son away at school—6 children. Before this week we had 1 Mac (mine) and 5 PCs (my wife’s, my two college kids have 1 each, 1 for my son in high school, and 1 shared by the others, as well as a Linux system for storage.
First, the mother board on the Linux box when bad. After struggling with it, I decided to replace it. To replace it, I bought a Apple Power Mac G4 (my notebook is a PowerBook G4). I bought it for $99 plus shipping from Mac of All Trades. $99! A friend gave us a second Power Mac G4. The friend called me up a few days later and said Mac of All Trades had $79 Power Macs, just like the one I bought. Did I want to buy another? I did! $79 for a computer! $79 for a very usable computer. For what? For web surfing. For music downloads. For Facebooking. For You Tubing. For writing documents and otherwise doing homework.
For heavy-duty music or photo editing? No. Software development? Probably not. More than adequate? A lot more than adequate.
And I forgot this about a new Mac, old, used, or otherwise. You plug it in, turn it on, confirm security settings (they are, after all, on my home network), and it is up and on the network, working. I mean in less than 5 minutes.
So, when the other new, old Mac shows up, it will be: 5 PCs and 4 Macs. So far. 🙂
On inexpensive vodka
I look in on lifehacker via my news feed aggregator. Today, an entry pointed to Top Shelf Vodka, Bottom Shelf Price, which substantiated something I always suspected. But, the reason I am posting this is this sentence which really tickled my fancy (as we used to say in the old days).
It is an interesting read. But ignore the “James Bond” and Smirnoff” line. That was a tie-in from the movies, not the novels, which should be consider canon.
I’d argue that the ultimate mark of a good vodka is that you can pull it out of the freezer, pour yourself a shot, and taste absolutely nothing except for the quick death of a few thousand brain cells.Okay, maybe the weekend has worn off already.
It is an interesting read. But ignore the “James Bond” and Smirnoff” line. That was a tie-in from the movies, not the novels, which should be consider canon.
3/25/09
Publishing from iCal to Google Calendar Solved
In Publishing from iCal to Google Calendar, I mentioned I found a solution to what I wanted to do. (Read the original post for details first.)
As I said in a comment on that post, After that I just follow the very easy to follow pointing and clicking in BusySync, connecting iCal calendars and Google Calendars. iCal does not have to be running. Periodically, BusySync syncs iCal and Google Calendars. It sits up in the menu bar and periodically spins for a few seconds.
After that I just follow the very easy to follow pointing and clicking in BusySync, connecting iCal calendars and Google Calendars. iCal does not have to be running. Periodically, BusySync syncs iCal and Google Calendars. It sits up in the menu bar and periodically spins for a few seconds.
Now, away from my Mac at home. I have access to my calendar on my iPod , as well as on Google Calendars.
, as well as on Google Calendars. 
I can change the calendar in either place. Doing it in Google Calendars means that anyone I share my calendars with can see the updates. It automatically syncs up to iCal at home and when I plug in at home, it syncs down to my iPod as well.
Exactly the behavior I was looking for. It’s not free. But, the $25 cost of the software is well worth it to me.
See the BusySync User Guide.
As I said in a comment on that post,
I did get a solution. BusyMac’s BusySync. It is not free, but it is only a one-time $25 purchase to do what I want to do. My iCal calendars easily publish to calendars on Google, and I can share them with my wife (and others).It was straightforward and easy to set-up. On my Google Calendars I set up calendars to match the calendars in iCal—just the ones I want to synchronize— and that are synchronized with my iPod touch. I even picked the same colors.
 After that I just follow the very easy to follow pointing and clicking in BusySync, connecting iCal calendars and Google Calendars. iCal does not have to be running. Periodically, BusySync syncs iCal and Google Calendars. It sits up in the menu bar and periodically spins for a few seconds.
After that I just follow the very easy to follow pointing and clicking in BusySync, connecting iCal calendars and Google Calendars. iCal does not have to be running. Periodically, BusySync syncs iCal and Google Calendars. It sits up in the menu bar and periodically spins for a few seconds.Now, away from my Mac at home. I have access to my calendar on my iPod
 , as well as on Google Calendars.
, as well as on Google Calendars. 
I can change the calendar in either place. Doing it in Google Calendars means that anyone I share my calendars with can see the updates. It automatically syncs up to iCal at home and when I plug in at home, it syncs down to my iPod as well.
Exactly the behavior I was looking for. It’s not free. But, the $25 cost of the software is well worth it to me.
See the BusySync User Guide.
3/24/09
Router Security
I was quoted in Kelly Jackson Higgins’s DarkReading column Hacking The Router Patching Conundrum.
I’ve blogged on the subject in Router and DMZ Best Practices.
I’ve blogged on the subject in Router and DMZ Best Practices.
3/14/09
My New iPod Touch
I ran over my iPod. It is not a great way to start this blog entry, but I feel so stupid, I wanted to get it out of the way.
In this blog entry I will first explain how it happened. Then I will tell you the remedy. And finally I will report on the restore/recovery process.
The damage.
I should explain how, because if you are like me, every time you read of someone running over their iPod, you think, “What, are you stupid? How could you do that?”
No. Never mind. I don’t think I will tell. It is stupid. I will say that it was in my man-bag, which is black, and apparently cannot be easily seen if dropped under the car when getting in, and … oh, man am I stupid. Anyway, I didn’t realize that it was damaged until I got to the coffee shop to meet a friend at 7:15 AM. As I sat down to my coffee and conversation, I pulled it out to turn it on and check email. Right away I knew what had happened.
It wasn’t crushed, nor was the glass cracked, but there were horizontal lines on the screen. When I powered it up, nothing showed except the very top of the screen. I saw that the wireless was working. So was the lock. Plenty of battery power. And the time was right, as I could tell from the top half of the time that was showing. I played with it a bit, seeing if I could affect a change, but even if I could slide the “unlock” slider (that I could not see), and if I could then miraculously type in the passcode without seeing anything except the top quarter inch of the screen, what would it tell me? It was broken
Blast it.
The remedy.
I tried to remember when I bought it. Was it still under warranty? Almost surely not. I erroneously (it would turn out) thought that it was 90 days. I bought it at Best Buy. Maybe I bought their extended care plan. My wife does for the kids’ Nintendo handhelds. It allows replacement for any reason for 2 years, but, I never get those. Never. But, maybe I screwed up and did.
So, my plan was to go home, check the receipt, check my budget, and then with it head to Best Buy, with a side trip (it is on the way) to The Apple Store. Maybe they would just wink, shrug, and give me a new one. Actually, I was thinking that they could tell me how much to send it in to repair if, if it was repairable. I found that I bought it October 10, 2008. I did not get the extended care plan. But, I did have just enough in budget to buy a new one. Apple Store and leave it there for repair or on to Best Buy and a new one, but another $400.
At 10-ish, the Apple Store did not have a waiting line. Genius Jeff D did not laugh, smirk, or say, “What, are you stupid? How could you do that?” He looked up the serial number and my name and said, “The good news is it is still under warranty.” (Huh?) “I see you bought it November 2.” (I guess there is a lag between purchase at a reseller and registering the sale.) “The screen is not covered, except for replacing the iPod touch with a new one. It will cost you $199 plus tax.”
They call it a “repair,” but to repair it Apple takes the broken iPod to salvage parts and gives a new one. So, after a few minutes I had a new iPod touch.
Restoring.
Jeff told me, “Just plug it in and it will notice it is a new iPod and it will ask you if you want to restore everything from your library and a backup.” It did not. But, it was close. Maybe I did something wrong. But, it did no damage.
iTunes recognized it as a new iPod. It asked if I wanted to sync with my Library. I did. It took awhile, but everything was added to the new iPod including my calendar entries and Contacts. But, nothing else. I mean, the App locations (which screen each was on) was wrong, but that is minor. I opened Notes and it was empty. No knowledge of my wireless access points. No data was saved in these other applications.
I know it regularly does something called a back-up. How to recover? I looked in iTunes help. “Recover?” No results. “Restore?” It tells you how to restore factory settings. I had to look on the Internet to find that Command-Control on the iPod name in iTunes brings down a menu that includes Backup and Restore from Backup.
Under Restore from Backup, it gave me 3 different Backups to pick from with no real indication of when they were made. (I found out that going to Preferences and Devices show the names, the order, and the date the backup was made. Cool, but I think it should be obvious in the Restore window.)
After the Restore, I found the data from Settings and every other App—Notes, Weather, Bible Reader, eBook, games, etc.—restored from the previous day. Good deal!
(All App data restored except LockBox Pro. I used that to cryptographically hold passwords and other such information. It worked great. It just does not survive being backed up and restored. I had the right number of records. They had just lost their labels and data. Out went LockBox Pro, and in went mSecure, which allows storing a backup on the computer. I’m good to go.)
[Addeddum: Wireless passwords did not survive either.]
Lessons learned.
First, if I drop my iPod, I will look until I find it, and I will never move the car if I lost it when anywhere near it. Next, I will always check in with The Apple store, as I did. Last, it really does back it up. I am so glad I do and did, and that I back up my files to an external drive. I didn’t need that last bit, but by backing up my iPod with iTunes, the whole ordeal took hours instead of days or weeks.
Did I mention that this happened on Friday the 13th?
In this blog entry I will first explain how it happened. Then I will tell you the remedy. And finally I will report on the restore/recovery process.
The damage.
I should explain how, because if you are like me, every time you read of someone running over their iPod, you think, “What, are you stupid? How could you do that?”
No. Never mind. I don’t think I will tell. It is stupid. I will say that it was in my man-bag, which is black, and apparently cannot be easily seen if dropped under the car when getting in, and … oh, man am I stupid. Anyway, I didn’t realize that it was damaged until I got to the coffee shop to meet a friend at 7:15 AM. As I sat down to my coffee and conversation, I pulled it out to turn it on and check email. Right away I knew what had happened.
It wasn’t crushed, nor was the glass cracked, but there were horizontal lines on the screen. When I powered it up, nothing showed except the very top of the screen. I saw that the wireless was working. So was the lock. Plenty of battery power. And the time was right, as I could tell from the top half of the time that was showing. I played with it a bit, seeing if I could affect a change, but even if I could slide the “unlock” slider (that I could not see), and if I could then miraculously type in the passcode without seeing anything except the top quarter inch of the screen, what would it tell me? It was broken
Blast it.
The remedy.
I tried to remember when I bought it. Was it still under warranty? Almost surely not. I erroneously (it would turn out) thought that it was 90 days. I bought it at Best Buy. Maybe I bought their extended care plan. My wife does for the kids’ Nintendo handhelds. It allows replacement for any reason for 2 years, but, I never get those. Never. But, maybe I screwed up and did.
So, my plan was to go home, check the receipt, check my budget, and then with it head to Best Buy, with a side trip (it is on the way) to The Apple Store. Maybe they would just wink, shrug, and give me a new one. Actually, I was thinking that they could tell me how much to send it in to repair if, if it was repairable. I found that I bought it October 10, 2008. I did not get the extended care plan. But, I did have just enough in budget to buy a new one. Apple Store and leave it there for repair or on to Best Buy and a new one, but another $400.
At 10-ish, the Apple Store did not have a waiting line. Genius Jeff D did not laugh, smirk, or say, “What, are you stupid? How could you do that?” He looked up the serial number and my name and said, “The good news is it is still under warranty.” (Huh?) “I see you bought it November 2.” (I guess there is a lag between purchase at a reseller and registering the sale.) “The screen is not covered, except for replacing the iPod touch with a new one. It will cost you $199 plus tax.”
They call it a “repair,” but to repair it Apple takes the broken iPod to salvage parts and gives a new one. So, after a few minutes I had a new iPod touch.
Restoring.
Jeff told me, “Just plug it in and it will notice it is a new iPod and it will ask you if you want to restore everything from your library and a backup.” It did not. But, it was close. Maybe I did something wrong. But, it did no damage.
iTunes recognized it as a new iPod. It asked if I wanted to sync with my Library. I did. It took awhile, but everything was added to the new iPod including my calendar entries and Contacts. But, nothing else. I mean, the App locations (which screen each was on) was wrong, but that is minor. I opened Notes and it was empty. No knowledge of my wireless access points. No data was saved in these other applications.
I know it regularly does something called a back-up. How to recover? I looked in iTunes help. “Recover?” No results. “Restore?” It tells you how to restore factory settings. I had to look on the Internet to find that Command-Control on the iPod name in iTunes brings down a menu that includes Backup and Restore from Backup.
Under Restore from Backup, it gave me 3 different Backups to pick from with no real indication of when they were made. (I found out that going to Preferences and Devices show the names, the order, and the date the backup was made. Cool, but I think it should be obvious in the Restore window.)
After the Restore, I found the data from Settings and every other App—Notes, Weather, Bible Reader, eBook, games, etc.—restored from the previous day. Good deal!
(All App data restored except LockBox Pro. I used that to cryptographically hold passwords and other such information. It worked great. It just does not survive being backed up and restored. I had the right number of records. They had just lost their labels and data. Out went LockBox Pro, and in went mSecure, which allows storing a backup on the computer. I’m good to go.)
[Addeddum: Wireless passwords did not survive either.]
Lessons learned.
First, if I drop my iPod, I will look until I find it, and I will never move the car if I lost it when anywhere near it. Next, I will always check in with The Apple store, as I did. Last, it really does back it up. I am so glad I do and did, and that I back up my files to an external drive. I didn’t need that last bit, but by backing up my iPod with iTunes, the whole ordeal took hours instead of days or weeks.
Did I mention that this happened on Friday the 13th?
3/13/09
Switching from PC to Mac
My “pc2mac” label on this blog started with my move from the PC to the Mac platform back in August 2005. (See Dude, You’re Getting a Mac!)
I just read a series of articles that I though would be interesting to anyone who arrived here wondering whether they should make the switch. (Short answer, “Yes!”)
Check out My Dad, the Switcher.
(Oh, and, Macs still end up being cheaper.)
I just read a series of articles that I though would be interesting to anyone who arrived here wondering whether they should make the switch. (Short answer, “Yes!”)
Check out My Dad, the Switcher.
(Oh, and, Macs still end up being cheaper.)
3/5/09
Cocktail resource
I just recently found The Cocktail Spirit with Robert Hess. If you are into or want to learn more about cocktail making or drinking, check it out.
2/25/09
Count the cost
A recent CIO article, “Ten steps for mitigating data risk during a merger, brought back memories. In 1998, the company I worked for, TIS, was acquired by Network Associates. One of my last acts as TIS’ CISO was to instruct the IT folks to keep firewall separation until they could get out to Santa Clara and install Gauntlet firewalls there.
You see, I rightly assumed that our network security postures were mismatched. Network Associates had only been an antivirus company (McAfee) and a packer sniffer company (Network General) glued together by money. It wasn’t that I didn’t think they cared about Internet security. I just thought that they had security tunnel vision. I also thought we knew more than they did about the subject and so had tighter controls in place.
A related story needs some background. In mid-November the United States Department of Defense suspended the use of so-called thumb drives, CDs, flash media cards, and all other removable data storage devices from their nets. You can read the article. It sounds like a smart move. Someone where I work pointed out that it really was untenable. Operational requirements in many organizations require moving data from one network to another by thumb drive.
I think the USB-ban was the wrong move. It looked like it was an attempt to curtain malware propagation—the Wired article cited said “to stop a worm assault”—. There are other things they could have done. If it was intended to fight a different problem, say memory sticks with sensitive data showing up in Afghan street markets, then there are other mitigations that could have been effective.
Given that the policy was changed, the recent action by the Air Force was the right one. You know the adage, “Security is a chain, and only as strong as its weakest link.” Both small and large organizations can learn from this. First, think through carefully the impact to your mission or business when implementing a policy change (even if your policy is not written down). Then, enforce it.
You see, I rightly assumed that our network security postures were mismatched. Network Associates had only been an antivirus company (McAfee) and a packer sniffer company (Network General) glued together by money. It wasn’t that I didn’t think they cared about Internet security. I just thought that they had security tunnel vision. I also thought we knew more than they did about the subject and so had tighter controls in place.
A related story needs some background. In mid-November the United States Department of Defense suspended the use of so-called thumb drives, CDs, flash media cards, and all other removable data storage devices from their nets. You can read the article. It sounds like a smart move. Someone where I work pointed out that it really was untenable. Operational requirements in many organizations require moving data from one network to another by thumb drive.
(A comment on an Army blog will come as no surprise. “This prohibition is now wide spread. We had it at Ft McPherson over a year ago. The easiest work-around is to e-mail files to/from each other and to outside (yahoo, msn, g-mail). For briefs, e-mail them to yourselves, then log onto the conference computer and get you own mail.” I predict bigger problems to come from these work-arounds. The Law of Unintended Consequences. But, I digress.)Given the order and the probably common reaction as in the above example, the Air Force has taken the next step necessary to maintain network integrity. Air Force Unplugs Bases’ Internet Connections.
I think the USB-ban was the wrong move. It looked like it was an attempt to curtain malware propagation—the Wired article cited said “to stop a worm assault”—. There are other things they could have done. If it was intended to fight a different problem, say memory sticks with sensitive data showing up in Afghan street markets, then there are other mitigations that could have been effective.
Given that the policy was changed, the recent action by the Air Force was the right one. You know the adage, “Security is a chain, and only as strong as its weakest link.” Both small and large organizations can learn from this. First, think through carefully the impact to your mission or business when implementing a policy change (even if your policy is not written down). Then, enforce it.
2/2/09
The Truth About Encrypting Your Notebook PCs
I’ve talked about the benefits of encrypting data on mobile computers. This, blog entry, Potentially Expensive Laptop Loss, points to some.
But, this xkcd web comic does inject some reality:
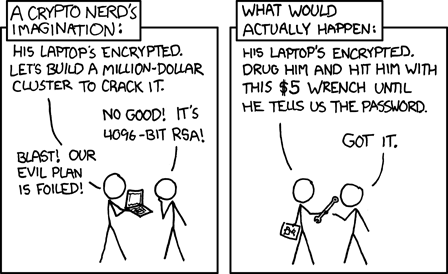
But, this xkcd web comic does inject some reality:

1/22/09
Will this White House have the first network security breach?
The Washington Post is reporting that Staff Finds White House in the Technological Dark Ages.
The article says that “Obama officials ran smack into the constraints of the federal bureaucracy yesterday, encountering a jumble of disconnected phone lines, old computer software, and security regulations forbidding outside e-mail accounts.”
I won’t repeat the rest of the article already states. I will point out one thing. A new administration seems to often (always?) be upset with the state of the information technology when it arrives at the White House. (See my blog entry Will Another President Call?) It makes sense, but still it seems that they were surprised that a move from the non-government-controlled campaign trail to the Oval office has IT security implications.
They will just have to figure out how to do what they think they need to within the constraints of the existing security policies and infrastructure. or they need to follow the policies that spell out how to change them. (And, regarding “security regulations forbidding outside e-mail accounts,” I just wonder if no one remembers what happened to Sarah Palin using Yahoo Mail.)
I’m no fan of the Windows Operating System. I am a fan of good-enough security and doing things in order. Perhaps the systems there are running “old computer software” because someone locked them down and it would be foolish to upgrade if they did the job. You secure it, you make sure it stays secure, and you change it only if you have to.
I work in a university lab. I cannot bring my personal PowerBook from home and plug it in to the lab’s inside network. I cannot use FaceBook or a handful of other applications that come with security risks and are not deemed related to the mission of the lab. It is not my home network. It is not my corporate network. It is the lab’s and fit’s the lab’s security policy.
Welcome to the big leagues. (Maybe future transition teams will add this to the checklist: look into IT infrastructure and security policies to determine impact on operations.”)
We also read Obama to get ‘super-encrypted’ BlackBerry. Yeah. Can it be secured? Sure. Will it be? We’ll see. Unless they slow down just a very little I suspect that this White House willhave the first network security breach.
The article says that “Obama officials ran smack into the constraints of the federal bureaucracy yesterday, encountering a jumble of disconnected phone lines, old computer software, and security regulations forbidding outside e-mail accounts.”
I won’t repeat the rest of the article already states. I will point out one thing. A new administration seems to often (always?) be upset with the state of the information technology when it arrives at the White House. (See my blog entry Will Another President Call?) It makes sense, but still it seems that they were surprised that a move from the non-government-controlled campaign trail to the Oval office has IT security implications.
They will just have to figure out how to do what they think they need to within the constraints of the existing security policies and infrastructure. or they need to follow the policies that spell out how to change them. (And, regarding “security regulations forbidding outside e-mail accounts,” I just wonder if no one remembers what happened to Sarah Palin using Yahoo Mail.)
I’m no fan of the Windows Operating System. I am a fan of good-enough security and doing things in order. Perhaps the systems there are running “old computer software” because someone locked them down and it would be foolish to upgrade if they did the job. You secure it, you make sure it stays secure, and you change it only if you have to.
I work in a university lab. I cannot bring my personal PowerBook from home and plug it in to the lab’s inside network. I cannot use FaceBook or a handful of other applications that come with security risks and are not deemed related to the mission of the lab. It is not my home network. It is not my corporate network. It is the lab’s and fit’s the lab’s security policy.
Welcome to the big leagues. (Maybe future transition teams will add this to the checklist: look into IT infrastructure and security policies to determine impact on operations.”)
We also read Obama to get ‘super-encrypted’ BlackBerry. Yeah. Can it be secured? Sure. Will it be? We’ll see. Unless they slow down just a very little I suspect that this White House willhave the first network security breach.
1/17/09
Publishing from iCal to Google Calendar
I thought that what I want to do should be easy. Straightforward even. I want to publish my iCal calendar to Google Calendars. But in days of “Googling,” I cannot find a straightforward solution. I find others who want to do the same thing and answers that tell them how to use a 3rd party product or intermediary site. I find the question asked—”How do I publish iCal calendars to Google Calendars”—to find answers discussing syncing calendars (how you can, how you cannot, and, again, other products to help).
I posted the following on the Apple Discussion groups:
I have a few calendars I want to publish so I can see them on Google Maps (and so others can), As I said, I want iCal (and Events on my iPod Touch) to be where I create events. I don’t need to sync calendars (except between my Mac and my iPod).
Now, I thought that I could publish directly to Google Calendars. In the mean time, I am publishing to iCal Exchange, run by a a guy running a free calendar sharing service. Publishing there worked flawlessly.
Then, in Google Calendars, I added each calendar I published to iCal Exchange by selecting Add by URL. It works fine. But, I didn’t think I should need an intermediary site. I believe I should be able to publish directly to my Google Calendars.
I’m waiting for an answer. I got an answer that works. See the comments, below.
I posted the following on the Apple Discussion groups:
I want to do something that apparently few others do. I have 6 calendars in iCal. (In iCal use them as other calendars use categories.) So, I have Personal, Birthdays, Meetings, School, etc.No answers yet.
I would like to publish them to Google Calendars. I want to use iCal (and the Calendar in my iPod touch) as my primary calendar. I want it mirrored on Google.
I looked at the “Life Hacker” blog pointed to in http://discussions.apple.com/thread.jspa?messageID=8360980�. There was one comment from someone who wanted to do what I want to do. The instructions create 6 (in my case) Google calendars. I don’t want that. I want to publish my iCal calendars to Google.
When I try to just publish Meetings, for example, to Google, I select a Calendar (Meeting) and select publish on a Private Server. I give the URL https://www.google.com/calendar/dav/fred%40avolio.com/user (which is my default calendar on my Google Apps account). I click Publish. The blue progress line goes left to right twice and then…
Publish failed for calendar “Meeting.” Calendar https://fred%40avolio.com@www.google.com/calendar/dav/fred@avolio.com/user/Meeting.ics could not be found.
I have a few calendars I want to publish so I can see them on Google Maps (and so others can), As I said, I want iCal (and Events on my iPod Touch) to be where I create events. I don’t need to sync calendars (except between my Mac and my iPod).
Now, I thought that I could publish directly to Google Calendars. In the mean time, I am publishing to iCal Exchange, run by a a guy running a free calendar sharing service. Publishing there worked flawlessly.
Then, in Google Calendars, I added each calendar I published to iCal Exchange by selecting Add by URL. It works fine. But, I didn’t think I should need an intermediary site. I believe I should be able to publish directly to my Google Calendars.
1/13/09
iPod Touch Wishlist
Recently in post on the Apple iPod discussion list, I included a “wishlist” for what I think is missing from the iPod touch. (Recall, I am using using my iPod touch as a PDA.)
The list I came up with off the top of my head:
The list I came up with off the top of my head:
- Copy and Paste. My reasons should be self-evident. I am using it as a hand held computer. I want to create calendar entries with text from e-mail or web pages. I want to send text from a web page in an email message.
- Mail should recognize calendar event attachments. I can click on a JPEG, Word Doc file, PDF, etc. and have the iPod touch do the right things. I want it to help me create an event.
- Memos/Notes synchronization. I have a lot of Notes. There is a 3rd party app that will do this, but I think iTunes should handle this. Not a killer as I found an app that was free to demo that I could use to move the many Memos I had on my Palm into Notes on my IPT.
- Task Manager. There are some in the App store. I don’t want to spend the money (though they are not expensive) as I think it should be connected with Calendar. So, I will wait for Apple on this as I think it is an obvious enhancement.
1/5/09
More in Antivirus and Macs
In what seems like a long time ago, 2006, I said, “Good-bye to AV,” and I gave my reasons. Recently, it seemed that Apple was suggesting otherwise. Because, Apple was suggesting otherwise.
The reason I am bringing this up, is because I recently read Verizon Business’s take on it (this is the old Risk Intelligence Team from TruSecure then Cybertrust, and the originators of the sorely missed “Hype or Hot” rating).
So, I am just pointing to this interesting analysis series:
The reason I am bringing this up, is because I recently read Verizon Business’s take on it (this is the old Risk Intelligence Team from TruSecure then Cybertrust, and the originators of the sorely missed “Hype or Hot” rating).
So, I am just pointing to this interesting analysis series:
Subscribe to:
Posts (Atom)