I needed a file I deleted a month or so ago, for my clinical class. It was of a session with a client, but I decided not to use it and, so, I deleted it. After all, it was 3 GB. It’s just that now, I wanted to do a “before and after” thing. (The client had done a tremendous amount of good work.)
I looked in Time Machine. It was not there. Maybe TM cleaned things up. Maybe I have something set to delete files so the backup drive doesn’t fill up too fast. I tried Crashplan. I put in the search string “.MP4.” It found some, but not the one I needed. Bummer!! Oh. Wait. “Display deleted files.” Check. Try again. BINGO! Brilliant.
I have CrashPlan Family Unlimited. Like getting a “replacement” policy for fire insurance, when you need it you’ll be glad you did.
Showing posts with label security. Show all posts
Showing posts with label security. Show all posts
6/17/11
5/12/10
“What are you looking for in a job?”
“Never again spend all day talking about nothing that will never get made (sic). I want to do real things; to think about real stuff, for real people, who need real things done, and I want to feel great about my environment where I do it. If I am going to spend 10 hours a day there, I need to like [the people there] a lot… to have a culture that works. Money is the reason people say they leave a job, but culture is the reason that money becomes an issue.”I was listening to the “43 Folders” podcast of Merlin Mann’s Time & Attention Talk at Rutgers. He was discussing the culture of meetings in different companies. As I listened I thought about a question someone had recently asked: what sorts of things are you looking for in a job?
When talking about job satisfaction and dissatisfaction, more than once I’ve had someone say, “That’s why they call it ‘work’ and not ‘vacation.'” While that sounds very clever, it does not address the other aspects of, and desires in, a job. I don’t know about you, but I am at the point in my life where benefits and salary are important, but they are second to having meaningful work to do and enjoying it, which includes the people, the environment, the culture, and the customer. Put another way, making a ton of money with fabulous benefits, producing wonderful and accurate reports that will sit on a shelf, sounds like Purgatory, if not Hell. (Granted, it beats doing all that for lousy pay.) Interesting and useful work trumps salary every time.
(Caveats: We need to eat. We need to be able to care for our health and that of our families. Sometimes, for a season, the most important thing is income. The economy could be so bad, and our particular skill set so out of step with what is needed, that we will do whatever we can to survive. I may be naïve, but I do hope that those times are rare.)
So, what does my perfect job look like, after things like working for and with an organization I can “get behind,” whose mission or purpose I can support and help advance? First, what Merlin described is a good start. Real challenges, real work, working with great people, for customers with real needs, who know they have them. I’ve been blessed with working with great people at every place I have worked, really, but that alone doesn’t offset “know-it-all” customers. Next, helping develop and guide others. This does not necessarily mean being a supervisor, though I have been very successful and satisfied doing that. Finally, the ability to work at home sometimes, is a great benefit.
I remember very well a recent job I had. I was a project manager leading an effort to assess the risks associated with an unbelievably large—really, unmeasurable—network. Further, we, the team, had an inkling that when we were done and the mathematics and statistical analyses were all proven, the final report would be put on a shelf. How did I keep from going crazy? I concentrated on the task at hand, certainly, but I also focused on the individuals on my team, helping them get through it, and preparing them for better work, better times. The result was sanity for me, the required “shelf-ware” for the satisfied customer, and—though not my goal—an excellent performance rating for me.
Looking at it from the other side, “Best jobs?” My top jobs—after my grad school assistantship—were working for DEC, working for TIS, and working for myself (Avolio Consulting).
DEC. Great people, challenging work, a lot of customers and sales people to bring together and for whom to provide “interpretive services” (we spoke “techie”). In my latter time at DEC, I was connected with developers and product managers in engineering, and the best group of peers in the field, worldwide. I was able to travel, had opportunities to teach, and earned a voice in the process of how and where the products went. I also supervised the best team of sales engineers I could ever imagine.
TIS. I was employee #78, or something. Small company, that I helped grow. “A fun place to work,” was a stated goal of Steve Walker, and it was. Again, I had the opportunity to grow in my influence, to mentor others, write, and speak. We had a great work environment, great corporate culture, and free lunch, coffee, and soft drinks. The people were great, and we still meet once a year for a reunion and party. I was influential in where the products and the company went.
Avolio Consulting.Great commute. No, just kidding, though I really liked that. Business was good, so I picked and chose my clients. The work was diverse: 1/3 consulting, 1/3 writing, and 1/3 teaching. The pay was great, but I reserved the right to give away
services when the client could not afford me and the challenge was interesting. (On my “Rates” page I quoted Sherlock Holmes in “The Problem of Thor Bridge”: “My professional charges are upon a fixed scale. I do not vary them, save when I remit them altogether.”)
I loved the varied work. I loved the ability to make decisions and set direction. It was wonderful working for “real people, who need real things done,” and solving real problems.
I notice something. In none of these did I mention “clearances,” or “commutes,” or “network and computer security” (or “information assurance“). Those things are secondary. They are particulars. In each of them, I did mention the same things that Merlin noted in his talk. I guess I agree with him. It may be different for you. I hope you find what you are looking for.
4/16/10
A Facebook friend is in trouble. Or is she?
Earlier today, I “retweeted” David Strom, who pointed to this story: Woman’s Facebook Account Hacked, Friends Ripped Off. The short version is after the account was broken into, the bad-guy sent a message to all of her friends currently on-line. “The message sent to her friends was a desperate plea for cash. … ‘hey I’m in London I just got mugged, my phone, my credit card was stolen, please send money so I can get home.'”
My friend, Diane, replied to my repost on Facebook, and said, “That’s scary! Thanks for sharing!”
Let’s do more. What should you do? You should first take a deep breath. (No, not now! I mean, when you see such a plea purported to be from a friend.) It may be a real emergency, but that does not mean there is no time to think.
And that’s the next thing to do. Think. Is your friend really out of the country? Do you have her phone number? Can you phone her to check? Is she still on Facebook? Can you ask her to verify her identity?
That’s the third thing. Verify. If she is a friend, surely there is a way to do this that is not already in her profile on Facebook. If you cannot come up with a way to verify her identity, then she is probably not close enough of a friend for you to wire $1000 to her. (Remember, she didn’t say she was stuck in an Afghan prison, she said “London.” Not so bad, really. She can wait a bit. And if she says she is in an Afghan prison, don’t believe it. They do not have Internet-connected computers in the cells. At least I doubt it.) In fact, that is what the victim recommends in the news story.
Breath. Think. Verify.
My friend, Diane, replied to my repost on Facebook, and said, “That’s scary! Thanks for sharing!”
Let’s do more. What should you do? You should first take a deep breath. (No, not now! I mean, when you see such a plea purported to be from a friend.) It may be a real emergency, but that does not mean there is no time to think.
And that’s the next thing to do. Think. Is your friend really out of the country? Do you have her phone number? Can you phone her to check? Is she still on Facebook? Can you ask her to verify her identity?
That’s the third thing. Verify. If she is a friend, surely there is a way to do this that is not already in her profile on Facebook. If you cannot come up with a way to verify her identity, then she is probably not close enough of a friend for you to wire $1000 to her. (Remember, she didn’t say she was stuck in an Afghan prison, she said “London.” Not so bad, really. She can wait a bit. And if she says she is in an Afghan prison, don’t believe it. They do not have Internet-connected computers in the cells. At least I doubt it.) In fact, that is what the victim recommends in the news story.
Breath. Think. Verify.
3/31/10
Old security flaws
Going back to my notes of things that I set aside to discuss or to comment on, I find a February 3 Computerworld article, Old security flaws still a major cause of breaches, says report. Its first line states “an over emphasis on tackling new and emerging security threats maybe causing companies to overlook older for more frequently exploited vulnerabilities, according to a recent report.” As I see it, the old but more common security threats—the old, but more common vulnerabilities—are less interesting, especially for newer security practitioners. Therefore, they get less serious attention.
The article makes some recommendations, including knowing your network assets. In other words, knowing what is is on your network, and knowing if it is behaving as you expect, will enhance your security posture.
I add the following:
The article makes some recommendations, including knowing your network assets. In other words, knowing what is is on your network, and knowing if it is behaving as you expect, will enhance your security posture.
I add the following:
- Know your network’s security posture. “Water seeks its own level.” Nowhere will it be higher than its lowest point. Or if you prefer, “a boat is only as strong as its weakest rower.” Network security is only as strong as its weakest component.
- Next, enforce existing security policies or remove them. Too many exceptions lower a network’s security posture and makes managing its security nearly impossible.
- If you are relying on reviewing log files, and associated port- and site-blocking as an important part of your network security, then you have already lost.
The Never-ending Battle
I remember in the late 1950 and early 60s watching the television program “The Adventures of Superman.” In the famous opening credits, (“Look up in the sky! It’s a bird! It’s a plane! It’s Superman!”), the narrator goes on to say, “and who, disguised as Clark Kent, mild-mannered reporter for a great metropolitan newspaper, fights a never-ending battle for truth, justice, and the American way!” Superman had his never-ending battles and we have ours. One of those is relying on reviewing log files, and associated port- and site-blocking as an important part of your network security. (I bring this up in Old security flaws.)
I know of a large network installation, that is fairly secure, but does rely on port- and site-blocking. Recently, someone tried using a file-syncing service, called Dropbox. As it’s description says, “Dropbox allows you to sync your files online and across your computers automatically.” You know? One uses it instead of carrying around a thumb-drive. There is a web interface and applications on Windows, Mac OS X, and iphone/iPod touch.
Now, as one can imagine, it is against many corporation’s security policy. Why? Here is the picture. At one end is a home computer. That could be “secure enough.” At the other end is a work computer. Same story. In between is a web site, in this case, inbox.com’s web site. I am not suggesting that their server and service is insecure. I don’t know. Did you catch that? Those three words are very significant when we are discussing network security matters. You are extending your security perimeter to include a web site belonging to someone else, administered by someone else, and under the corporate (command) management of someone else. Three strikes.
Someone tried to use dropbox, and could between his home and the web site, and between his iPhone and the web site, but not between his desktop at work and dropbox.com website, neither by the web site, nor from the dropbox application program. To him, it was no big dea. He did not have a business need for it; he was just trying it out.
A few days later, he received an email from someone in the company IT department of his company, who asked what I was doing? The log files showed repeated attempts to connect to dropbox from his IP address! He asked what policy was it against, and he was pointed to a policy that talked about proprietary, sensitive, and “for official use only” information. That is a good policy, but it did not apply. There was no sensitive information involved.
He also told the person from IT, that he had successfully used SugarSync, a program that does the same exact thing on the same platforms. IT did not flag that or block that. It didn’t know about it. SHould it be blocked? What about EverNote? Similar attributes. Potentially, similar risks.
Do you see the problem? Either this sort of thing is permitted or it is not. It cannot be permitted when we do not know enough to block access to a site, but denied when we do. If we cannot affectively block it, we block it when we can and we create, publicize, and enforce a well-vetted policy. The policy plus enforcement is key. And by enforcement, I don’t just mean mitigation. I mean following through with consequences when the policy is ignored. And possible consequences will be spelled out in the policy as well. Otherwise you are involved in a never-ending battle.
I know of a large network installation, that is fairly secure, but does rely on port- and site-blocking. Recently, someone tried using a file-syncing service, called Dropbox. As it’s description says, “Dropbox allows you to sync your files online and across your computers automatically.” You know? One uses it instead of carrying around a thumb-drive. There is a web interface and applications on Windows, Mac OS X, and iphone/iPod touch.
Now, as one can imagine, it is against many corporation’s security policy. Why? Here is the picture. At one end is a home computer. That could be “secure enough.” At the other end is a work computer. Same story. In between is a web site, in this case, inbox.com’s web site. I am not suggesting that their server and service is insecure. I don’t know. Did you catch that? Those three words are very significant when we are discussing network security matters. You are extending your security perimeter to include a web site belonging to someone else, administered by someone else, and under the corporate (command) management of someone else. Three strikes.
Someone tried to use dropbox, and could between his home and the web site, and between his iPhone and the web site, but not between his desktop at work and dropbox.com website, neither by the web site, nor from the dropbox application program. To him, it was no big dea. He did not have a business need for it; he was just trying it out.
A few days later, he received an email from someone in the company IT department of his company, who asked what I was doing? The log files showed repeated attempts to connect to dropbox from his IP address! He asked what policy was it against, and he was pointed to a policy that talked about proprietary, sensitive, and “for official use only” information. That is a good policy, but it did not apply. There was no sensitive information involved.
He also told the person from IT, that he had successfully used SugarSync, a program that does the same exact thing on the same platforms. IT did not flag that or block that. It didn’t know about it. SHould it be blocked? What about EverNote? Similar attributes. Potentially, similar risks.
Do you see the problem? Either this sort of thing is permitted or it is not. It cannot be permitted when we do not know enough to block access to a site, but denied when we do. If we cannot affectively block it, we block it when we can and we create, publicize, and enforce a well-vetted policy. The policy plus enforcement is key. And by enforcement, I don’t just mean mitigation. I mean following through with consequences when the policy is ignored. And possible consequences will be spelled out in the policy as well. Otherwise you are involved in a never-ending battle.
2/22/10
Security Axioms, Good, Old Stuff
It has been years since I published a list of Security Axioms on my web page. Note, I didn’t write “My” security axioms. They are old, probably timeless, and too-often forgotten.
Bill Murray, in his Thinking About Security blog mentions some that fit right in, in his post “Effective” Security.
Bill Murray, in his Thinking About Security blog mentions some that fit right in, in his post “Effective” Security.
2/21/10
Phishing and Phacebook Applications
Oops. meant “Facebook.”
Email messages about millions in contract money waiting to be paid to you for work you did years ago in Nigeria. Or an inheritance waiting for you because someone in Ghana heard about your Christian charity.
Most of us are smart enough to know that those are scams. (As I wrote in
Internet Safety, “No widow in some foreign country has heard of what a kind-hearted, trustworthy person you are, no matter how kind-hearted and trustworthy you are.” And, “Did you really do business in another country and forget that they still owed you $75,000?”)
They feed on our greed and on our pride, right?
Facebook applications like these are similar:
Anyway, it doesn’t matter why. What matters it they do get attention. They are also prime candidates for applications that contain malware (things that trigger viruses, etc.).
My friends on Facebook should not take offense at this, but I do not add applications. I don’t trust those applications. Also, I’d rather interact with you on Facebook with words rather than snowballs, pumpkins, or whatever.
No one will listen, but I recommend going into your Facebook and removing any Application you don’t remember adding or whose purpose you don’t understand. (I mean, what could happen? No more stray cows in your corn?)
(I assume you know what phishing is. The Wikipedia definition of phishing is good.)
Email messages about millions in contract money waiting to be paid to you for work you did years ago in Nigeria. Or an inheritance waiting for you because someone in Ghana heard about your Christian charity.
Most of us are smart enough to know that those are scams. (As I wrote in
Internet Safety, “No widow in some foreign country has heard of what a kind-hearted, trustworthy person you are, no matter how kind-hearted and trustworthy you are.” And, “Did you really do business in another country and forget that they still owed you $75,000?”)
They feed on our greed and on our pride, right?
Facebook applications like these are similar:
- “Who secretly thinks you are hot?”
- “Who has blocked you?”
Anyway, it doesn’t matter why. What matters it they do get attention. They are also prime candidates for applications that contain malware (things that trigger viruses, etc.).
My friends on Facebook should not take offense at this, but I do not add applications. I don’t trust those applications. Also, I’d rather interact with you on Facebook with words rather than snowballs, pumpkins, or whatever.
No one will listen, but I recommend going into your Facebook and removing any Application you don’t remember adding or whose purpose you don’t understand. (I mean, what could happen? No more stray cows in your corn?)
(I assume you know what phishing is. The Wikipedia definition of phishing is good.)
12/23/09
The Real Threat?
Back in 1979, just out of grad school, I got my first real job working as a software developer (we used to be called “programmers” in the olden days). I learned the C programming language then and did my software development on a Digital Equipment Corporation PDP-11/70 minicomputer running 6th edition UNIX. And for the first time, I was using a multiuser computer which could be crashed by a non-privileged user doing non-privileged things. I mean, an error in Charlie’s or Mike’s (never mine!) code could crash the whole machine. “Why doesn’t the operating system protect against such things?”
As I said, that was 1979. 30 years later, in September 2009, my friend David Strom, citing a report from the SANS Institute on top cyber security risks, wrote “Unpatched applications are the real threat.” Are they? I reiterated what I asked 30 years ago: “Why doesn’t the operating system protect against such things?”
Quoting the SANS report, he writes, “Most web site owners fail to scan effectively for the common flaws,” and “TippingPoint reported that vulnerabilities that were more than two years old were still waiting for patches.”
Patching? The SANS report is a good reminder of what can and should be done in the short term. But, it is clear that, while patching is useful (I won’t even write “important”), it should only be important for data integrity or program availability, not for security of the data or of the system. The hardware and software system should protect against such things. The computer science world has been flirting with “trusted computing” and trusted operating systems for years. The “real threat?” Operating systems we still cannot trust to effectively control and contain user-level applications.
As I said, that was 1979. 30 years later, in September 2009, my friend David Strom, citing a report from the SANS Institute on top cyber security risks, wrote “Unpatched applications are the real threat.” Are they? I reiterated what I asked 30 years ago: “Why doesn’t the operating system protect against such things?”
Quoting the SANS report, he writes, “Most web site owners fail to scan effectively for the common flaws,” and “TippingPoint reported that vulnerabilities that were more than two years old were still waiting for patches.”
Patching? The SANS report is a good reminder of what can and should be done in the short term. But, it is clear that, while patching is useful (I won’t even write “important”), it should only be important for data integrity or program availability, not for security of the data or of the system. The hardware and software system should protect against such things. The computer science world has been flirting with “trusted computing” and trusted operating systems for years. The “real threat?” Operating systems we still cannot trust to effectively control and contain user-level applications.
“Senate Panel Agrees with Avolio”
Okay, the headline actually says, Senate Panel: 80 Percent of Cyber Attacks Preventable, but basically the panel said what I have said in over 60 different blog entries (according to this search on “same old”). The article by Kim Zetter opens with this statement:
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
If network administrators simply instituted proper configuration policies and conducted good network monitoring, about 80 percent of commonly known cyber attacks could be prevented.This October 2009 Wired article is an example of what I’m (and they are) talking about. The headline states “Time Warner Cable Exposes 65,000 Customer Routers to Remote Hacks.” It goes on to mention “The device is installed with default configurations.” (See what I wrote about default configurations and what to do about them at Top Ten Security Threats, but in this case it would not have helped as Time-Warner did not permit changing the router in question.)
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
9/21/09
Be Careful With Those Firefox Extensions
People who know me from my consulting and teaching days, or who have read my web site from my consulting days, have read my blog. or have been in a class I taught, know that I am a pretty cautious guy when it comes to the Internet.
Today, via web mail, I was checking my personal (non-APL) email. I saw one of the messages was from Hallmark Postcards, saying I had a postcard from someone. Now, I already knew that it was spam, just from that information. What I should have done was just check the box next to it and click on “Report Spam.” Instead I opened the message. No problem. I saw the URL for the card, so I “hovered” my mouse over it. It was “postcard.exe.” Into the spam folder with you, sucker!
A few minutes later I got a call from someone in the IT department here at APL. One of our security devices indicated I tried to download that file. It blocked the download and reported it. Now, the Windows executable would have done nothing on my Mac, and recall I did not click on it to download it. What had happened?
I looked through the add-ons and extensions I had in Firefox. Sure enough, amidst the security-related add-ons, I also had added Interclue, “Your Personal Link Preview Multitool.” It promises, “Before you click the link: Hover your mouse pointer over the link, and a Linkclue icon will appear. Rest your mouse on the icon, and up pops an enhanced summary of the linked page.”
Hmmm. I don’t think it actually tried (or tries) to download anything. I think that our security software saw this in the stream and triggered an alarm. (On the other hand, what does it mean to “preview” an executable? I’m not sure, and I didn’t need Interclue enough to want to keep it. I uninstalled it and restarted Firefox.
Update
I heard from my co-worker in the IT department. He writes:
Today, via web mail, I was checking my personal (non-APL) email. I saw one of the messages was from Hallmark Postcards, saying I had a postcard from someone. Now, I already knew that it was spam, just from that information. What I should have done was just check the box next to it and click on “Report Spam.” Instead I opened the message. No problem. I saw the URL for the card, so I “hovered” my mouse over it. It was “postcard.exe.” Into the spam folder with you, sucker!
A few minutes later I got a call from someone in the IT department here at APL. One of our security devices indicated I tried to download that file. It blocked the download and reported it. Now, the Windows executable would have done nothing on my Mac, and recall I did not click on it to download it. What had happened?
I looked through the add-ons and extensions I had in Firefox. Sure enough, amidst the security-related add-ons, I also had added Interclue, “Your Personal Link Preview Multitool.” It promises, “Before you click the link: Hover your mouse pointer over the link, and a Linkclue icon will appear. Rest your mouse on the icon, and up pops an enhanced summary of the linked page.”
Hmmm. I don’t think it actually tried (or tries) to download anything. I think that our security software saw this in the stream and triggered an alarm. (On the other hand, what does it mean to “preview” an executable? I’m not sure, and I didn’t need Interclue enough to want to keep it. I uninstalled it and restarted Firefox.
Update
I heard from my co-worker in the IT department. He writes:
What our network systems saw is the following exchange between your host and the remote serverI agree. Avoid this Firefox extension.Request from your host:This, of course, shows your host asking for postcard.exe and our Websense device referring your host to a block page thereby preventing the download. Your Firefox plug-in wants to provide a preview of the web page. To provide a preview, it apparently downloads the web page (or at least part of it). Otherwise, how would it know what the page looks like so it could provide a preview? It looks like a rather dangerous plug-in, one designed for a more friendly Internet.
GET /postcard.exe HTTP/1.1
Host: nn.nn.nn.nn
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US;
rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Cache-Control: no-cache
Pragma: no-cache
Reply to the request:
HTTP/1.1 302 Moved Temporarily
Date: Mon, 21 Sep 2009 14:05:36 GMT
Connection: close
Via: HTTP/1.1 localhost.localdomain (Websense-Content_Gateway/7.1.2 [c s f
])
Location:
http://nn.nn.nn.nn/cgi-bin/blockpage.cgi?ws-session=3741857785
Content-Length: 0
9/12/09
Safeguard your Notebook Computer
No matter how careful you are about physically protecting your small notebook computer, you need to plan for the worse. A few months ago, The Unofficial Apple Weblog (TUAW) had an article 9 things I learned from almost losing my MacBook Air. It is Mac-specific in the details, but no matter whether you have a MacBook, a Windows notebook, or something else, computers are getting smaller, disks are getting larger, and that raises the vulnerability to information loss. And no matter what you think, you have data on your computer that, in the wrong hands, could cost you money.
It reminded me of a few columns, not Mac-specific, I wrote years a few years back:
It reminded me of a few columns, not Mac-specific, I wrote years a few years back:
8/13/09
Strom Reviews Sendmail’s Senturion
My friend David Strom recently posted a video review of this enterprise e-mail management product from Sendmail, Inc. His review is at Webinformant.tv.
Sendmail has come a long way since I wrote this review of Sendmail Pro, over 9 years ago!
Sendmail has come a long way since I wrote this review of Sendmail Pro, over 9 years ago!
8/1/09
Time Machine System Restore
I have an 80GB disk waiting to be installed to upgrade my aging, bit still small, light, and useful PowerBook G4. Last week, I wrote to a friend, “Would have been a good day to swap disks out. :-)”
The PB was working fine. As I mentioned in System Back-ups, I have an external FireWire drive onto which TimeMachine backs up. Last
backup 10:30 that “fateful” morning. At 11 or so I decided I should run SuperDuper!, which I use to have a bootable copy of my PB. (I don’t do that automatically; the last time I did that was 2 weeks earlier, but Time Machine does the day-to-day—really hour-to-hour—file copy stuff.) Before I did that, I decided to check it out with Disk Utility.
I ran DU and got the error “Keys out of order… The Volume Macintosh HD could not be repaired. Error: File verify or repair failed. You are so hosed.” (I made up that last bit.)
I booted off of the FireWire Leopard partition, used Disk Utility on it and it still could not fix it. Now, I was a bit annoyed. There should be nothing in software that should hurt the disk structure so much that software cannot fix it. And I mean software from the vendor.
I was told that Disk Warrior would fix errors on the disk including this “Keys out of order.” A friend, who seems to have everything, had an unopened copy of Disk Warrior, which I tried. No joy. It could not fix it.
Hmmm. I was starting to think of that 80 GB disk sitting in its wrapper. But, that would entail spending time and tools to open my PowerBook. No, that would wait for another day.
I tried to Restore (in Disk Utility) from my Leopard partition I was running off of (FireWire drive, remember), to my Mac HD. It said their wasn’t enough space! Okay, I erased my Mac HD! There! Said the same thing.
Plan C, now. Restore from Time Machine. Following Apple’s Instructions, I booted from the install DVD, picked Restore from Time Machine, and… it worked. It worked beautifully.
Whew.
The PB was working fine. As I mentioned in System Back-ups, I have an external FireWire drive onto which TimeMachine backs up. Last
backup 10:30 that “fateful” morning. At 11 or so I decided I should run SuperDuper!, which I use to have a bootable copy of my PB. (I don’t do that automatically; the last time I did that was 2 weeks earlier, but Time Machine does the day-to-day—really hour-to-hour—file copy stuff.) Before I did that, I decided to check it out with Disk Utility.
I ran DU and got the error “Keys out of order… The Volume Macintosh HD could not be repaired. Error: File verify or repair failed. You are so hosed.” (I made up that last bit.)
I booted off of the FireWire Leopard partition, used Disk Utility on it and it still could not fix it. Now, I was a bit annoyed. There should be nothing in software that should hurt the disk structure so much that software cannot fix it. And I mean software from the vendor.
I was told that Disk Warrior would fix errors on the disk including this “Keys out of order.” A friend, who seems to have everything, had an unopened copy of Disk Warrior, which I tried. No joy. It could not fix it.
Hmmm. I was starting to think of that 80 GB disk sitting in its wrapper. But, that would entail spending time and tools to open my PowerBook. No, that would wait for another day.
I tried to Restore (in Disk Utility) from my Leopard partition I was running off of (FireWire drive, remember), to my Mac HD. It said their wasn’t enough space! Okay, I erased my Mac HD! There! Said the same thing.
Plan C, now. Restore from Time Machine. Following Apple’s Instructions, I booted from the install DVD, picked Restore from Time Machine, and… it worked. It worked beautifully.
Whew.
7/15/09
Schneier on North Korean Cyberattacks
The complete text is at http://www.schneier.com/blog/archives/2009/07/north_korean_cy.html.
Some great quotes:
Some great quotes:
- "What [the President] didn’t add was that those infections occurred because the Air Force couldn’t be bothered to keep its patches up to date. … Even this current incident is turning out to be a sloppily modified five-year-old worm that no modern network should still be vulnerable to."
- "Securing our networks doesn’t require some secret advanced NSA technology. It’s the boring network security administration stuff we already know how to do: keep your patches up to date, install good anti-malware software, correctly configure your firewalls and intrusion-detection systems, monitor your networks. And while some government and corporate networks do a pretty good job at this, others fail again and again."
- "The news isn’t the attacks, but that some networks had security lousy enough to be vulnerable to them."
7/10/09
Spammers need grammar lessons
“Hello from Ms vivian shaka, I am writing with the earnest prayer that my attention will meet favorably with you.”
I really want to reply and say, “Hey, Viv! What the heck does that even mean?! ‘My attenion will meet favorably with you,’ indeed!”
I really want to reply and say, “Hey, Viv! What the heck does that even mean?! ‘My attenion will meet favorably with you,’ indeed!”
4/22/09
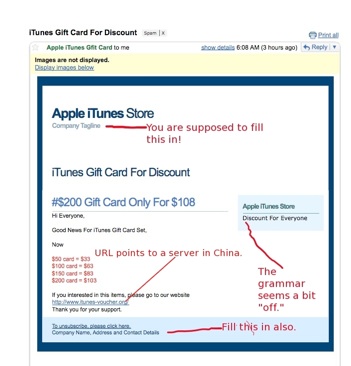
Note to a Chinese Phisher
4/14/09
On-line Backups
I have written about the importance of system back-ups many times before. I talk about it specifically in System Back-ups.
Today, in my news aggregater, Macworld reported on BackBlaze. BackBlaze is a $5/month online backup server and service for Macs and PCs, and has no limit to how much you can back up.
Also, The Unofficial Apple Weblog has a review with shiny pictures.
I’ve not tried it yet, but I intend to. The questions that have come to my mind are all the obvious ones. They answer some on their web page. For many of you, the important answer is “It is better than the backup scheme you currently have,” knowing that many of you (twice I wanted to write “most”) don’t backup at all.
If you try it, let me know what you think. I will do the same.
Today, in my news aggregater, Macworld reported on BackBlaze. BackBlaze is a $5/month online backup server and service for Macs and PCs, and has no limit to how much you can back up.
Also, The Unofficial Apple Weblog has a review with shiny pictures.
I’ve not tried it yet, but I intend to. The questions that have come to my mind are all the obvious ones. They answer some on their web page. For many of you, the important answer is “It is better than the backup scheme you currently have,” knowing that many of you (twice I wanted to write “most”) don’t backup at all.
If you try it, let me know what you think. I will do the same.
4/6/09
3/24/09
Router Security
I was quoted in Kelly Jackson Higgins’s DarkReading column Hacking The Router Patching Conundrum.
I’ve blogged on the subject in Router and DMZ Best Practices.
I’ve blogged on the subject in Router and DMZ Best Practices.
2/25/09
Count the cost
A recent CIO article, “Ten steps for mitigating data risk during a merger, brought back memories. In 1998, the company I worked for, TIS, was acquired by Network Associates. One of my last acts as TIS’ CISO was to instruct the IT folks to keep firewall separation until they could get out to Santa Clara and install Gauntlet firewalls there.
You see, I rightly assumed that our network security postures were mismatched. Network Associates had only been an antivirus company (McAfee) and a packer sniffer company (Network General) glued together by money. It wasn’t that I didn’t think they cared about Internet security. I just thought that they had security tunnel vision. I also thought we knew more than they did about the subject and so had tighter controls in place.
A related story needs some background. In mid-November the United States Department of Defense suspended the use of so-called thumb drives, CDs, flash media cards, and all other removable data storage devices from their nets. You can read the article. It sounds like a smart move. Someone where I work pointed out that it really was untenable. Operational requirements in many organizations require moving data from one network to another by thumb drive.
I think the USB-ban was the wrong move. It looked like it was an attempt to curtain malware propagation—the Wired article cited said “to stop a worm assault”—. There are other things they could have done. If it was intended to fight a different problem, say memory sticks with sensitive data showing up in Afghan street markets, then there are other mitigations that could have been effective.
Given that the policy was changed, the recent action by the Air Force was the right one. You know the adage, “Security is a chain, and only as strong as its weakest link.” Both small and large organizations can learn from this. First, think through carefully the impact to your mission or business when implementing a policy change (even if your policy is not written down). Then, enforce it.
You see, I rightly assumed that our network security postures were mismatched. Network Associates had only been an antivirus company (McAfee) and a packer sniffer company (Network General) glued together by money. It wasn’t that I didn’t think they cared about Internet security. I just thought that they had security tunnel vision. I also thought we knew more than they did about the subject and so had tighter controls in place.
A related story needs some background. In mid-November the United States Department of Defense suspended the use of so-called thumb drives, CDs, flash media cards, and all other removable data storage devices from their nets. You can read the article. It sounds like a smart move. Someone where I work pointed out that it really was untenable. Operational requirements in many organizations require moving data from one network to another by thumb drive.
(A comment on an Army blog will come as no surprise. “This prohibition is now wide spread. We had it at Ft McPherson over a year ago. The easiest work-around is to e-mail files to/from each other and to outside (yahoo, msn, g-mail). For briefs, e-mail them to yourselves, then log onto the conference computer and get you own mail.” I predict bigger problems to come from these work-arounds. The Law of Unintended Consequences. But, I digress.)Given the order and the probably common reaction as in the above example, the Air Force has taken the next step necessary to maintain network integrity. Air Force Unplugs Bases’ Internet Connections.
I think the USB-ban was the wrong move. It looked like it was an attempt to curtain malware propagation—the Wired article cited said “to stop a worm assault”—. There are other things they could have done. If it was intended to fight a different problem, say memory sticks with sensitive data showing up in Afghan street markets, then there are other mitigations that could have been effective.
Given that the policy was changed, the recent action by the Air Force was the right one. You know the adage, “Security is a chain, and only as strong as its weakest link.” Both small and large organizations can learn from this. First, think through carefully the impact to your mission or business when implementing a policy change (even if your policy is not written down). Then, enforce it.
Subscribe to:
Posts (Atom)