Back in 1979, just out of grad school, I got my first real job working as a software developer (we used to be called “programmers” in the olden days). I learned the C programming language then and did my software development on a Digital Equipment Corporation PDP-11/70 minicomputer running 6th edition UNIX. And for the first time, I was using a multiuser computer which could be crashed by a non-privileged user doing non-privileged things. I mean, an error in Charlie’s or Mike’s (never mine!) code could crash the whole machine. “Why doesn’t the operating system protect against such things?”
As I said, that was 1979. 30 years later, in September 2009, my friend David Strom, citing a report from the SANS Institute on top cyber security risks, wrote “Unpatched applications are the real threat.” Are they? I reiterated what I asked 30 years ago: “Why doesn’t the operating system protect against such things?”
Quoting the SANS report, he writes, “Most web site owners fail to scan effectively for the common flaws,” and “TippingPoint reported that vulnerabilities that were more than two years old were still waiting for patches.”
Patching? The SANS report is a good reminder of what can and should be done in the short term. But, it is clear that, while patching is useful (I won’t even write “important”), it should only be important for data integrity or program availability, not for security of the data or of the system. The hardware and software system should protect against such things. The computer science world has been flirting with “trusted computing” and trusted operating systems for years. The “real threat?” Operating systems we still cannot trust to effectively control and contain user-level applications.
12/23/09
“Senate Panel Agrees with Avolio”
Okay, the headline actually says, Senate Panel: 80 Percent of Cyber Attacks Preventable, but basically the panel said what I have said in over 60 different blog entries (according to this search on “same old”). The article by Kim Zetter opens with this statement:
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
If network administrators simply instituted proper configuration policies and conducted good network monitoring, about 80 percent of commonly known cyber attacks could be prevented.This October 2009 Wired article is an example of what I’m (and they are) talking about. The headline states “Time Warner Cable Exposes 65,000 Customer Routers to Remote Hacks.” It goes on to mention “The device is installed with default configurations.” (See what I wrote about default configurations and what to do about them at Top Ten Security Threats, but in this case it would not have helped as Time-Warner did not permit changing the router in question.)
Another Wired article pointing out a similar problem states, Scan of Internet Uncovers Thousands of Vulnerable Embedded Devices
Why don’t we get it? None of it is expensive. None of this is hard. None of it is new.
Evernote
Many have reviewed Evernote, and months have gone by since I first mentioned it in my blog. I will briefly discuss how and why I use Evernote and point to some other helpful blog posts.
In my quest to get things done, I used to make use of email and of my PDA to keep task lists and to remind me of things I did not want to forget. (As the senior Dr. Henry Jones says, in Indiana Jones and the Last Crusade says, “I wrote them down in my Diary so that I wouldn’t have to remember.”) If I found something on the web that I wanted to download or read, but didn’t have the time to deal with at the moment, I would send myself emails with the subject “tryme” or “readme.” When I got home in the evening, I would take care of them by actually downloading something I wanted to try or reading something I wanted to read (on my iPod touch screen, or by printing).
Also, as I have mentioned, I make extensive use of Notes in my PDAs; I used to use Memos on Palm, and now Notes on my iPod touch. Then I started reading about Evernote. I read 7 Ways to Use Evernote. I also read 9 Ways I use Evernote, and How To Use Evernote to Remember Everything, Part 1 and Part2.
I started using Evernote to capture the things I previously emailed. I did this on my home PowerBook Pro of on mywork MacBook Pro.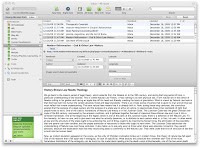 The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch.
The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch. 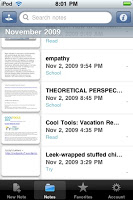
The more I use Evernote, the more I like it, and the more ways I find to use it.
In my quest to get things done, I used to make use of email and of my PDA to keep task lists and to remind me of things I did not want to forget. (As the senior Dr. Henry Jones says, in Indiana Jones and the Last Crusade says, “I wrote them down in my Diary so that I wouldn’t have to remember.”) If I found something on the web that I wanted to download or read, but didn’t have the time to deal with at the moment, I would send myself emails with the subject “tryme” or “readme.” When I got home in the evening, I would take care of them by actually downloading something I wanted to try or reading something I wanted to read (on my iPod touch screen, or by printing).
Also, as I have mentioned, I make extensive use of Notes in my PDAs; I used to use Memos on Palm, and now Notes on my iPod touch. Then I started reading about Evernote. I read 7 Ways to Use Evernote. I also read 9 Ways I use Evernote, and How To Use Evernote to Remember Everything, Part 1 and Part2.
I started using Evernote to capture the things I previously emailed. I did this on my home PowerBook Pro of on mywork MacBook Pro.
 The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch.
The notes were accessible on both and on my iPod touch. I took brief reminder notes on my touch. I started taking notes Evernote in the classes I was taking using my PowerBook, I’d take notes on my iPod touch when reading for the classes, and I would study reading (and searching) through both on my touch. 
The more I use Evernote, the more I like it, and the more ways I find to use it.
Subscribe to:
Posts (Atom)

